Researchers Can Duplicate Keys from the Sounds They Make in Locks
Researchers have demonstrated that they can make a working 3D-printed copy of a key just by listening to how the key sounds when inserted into a lock. And you don’t need a fancy mic — a smartphone or smart doorbell will do nicely if you can get it close enough to the lock.
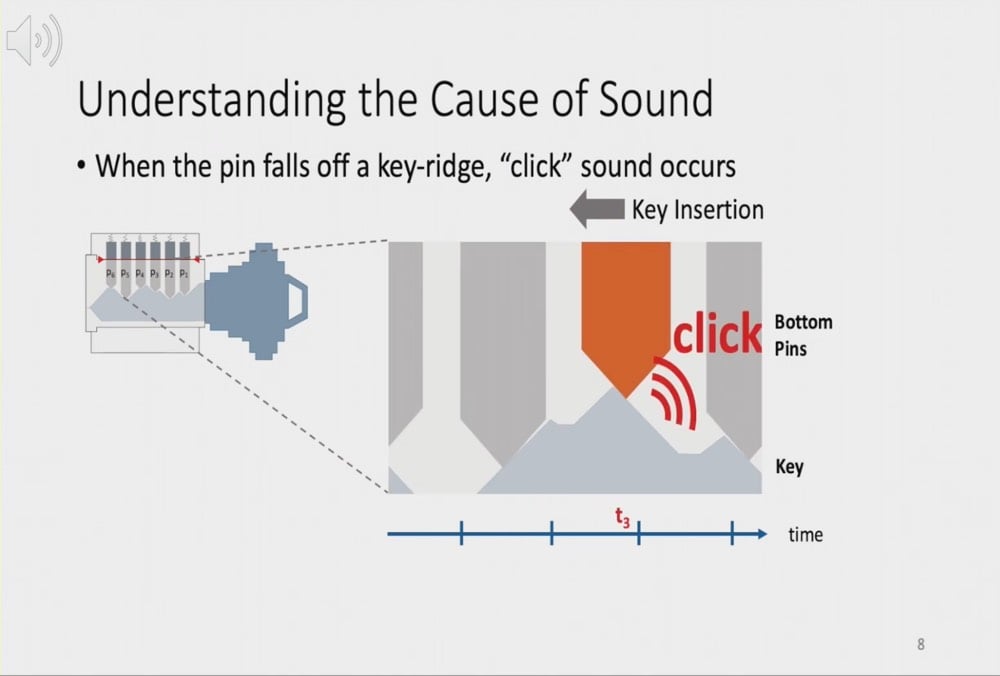
The next time you unlock your front door, it might be worth trying to insert your key as quietly as possible; researchers have discovered that the sound of your key being inserted into the lock gives attackers all they need to make a working copy of your front door key.
It sounds unlikely, but security researchers say they have proven that the series of audible, metallic clicks made as a key penetrates a lock can now be deciphered by signal processing software to reveal the precise shape of the sequence of ridges on the key’s shaft. Knowing this (the actual cut of your key), a working copy of it can then be three-dimensionally (3D) printed.
How Soundarya Ramesh and her team accomplished this is a fascinating read.
Once they have a key-insertion audio file, SpiKey’s inference software gets to work filtering the signal to reveal the strong, metallic clicks as key ridges hit the lock’s pins [and you can hear those filtered clicks online here]. These clicks are vital to the inference analysis: the time between them allows the SpiKey software to compute the key’s inter-ridge distances and what locksmiths call the “bitting depth” of those ridges: basically, how deeply they cut into the key shaft, or where they plateau out. If a key is inserted at a nonconstant speed, the analysis can be ruined, but the software can compensate for small speed variations.
The result of all this is that SpiKey software outputs the three most likely key designs that will fit the lock used in the audio file, reducing the potential search space from 330,000 keys to just three. “Given that the profile of the key is publicly available for commonly used [pin-tumbler lock] keys, we can 3D-print the keys for the inferred bitting codes, one of which will unlock the door,” says Ramesh.
Here’s Ramesh presenting her research at a conference back in March.
This reminded me of a couple of things. If you have a photo of a key, you can make a copy of it. And if you record high speed video of objects like plants or potato chip bags, you can use the observed vibrations to reconstruct the sound near those objects. All these secrets lying out in the open, just waiting for clever technologies to hoover them up. (via @nicolatwilley)




Stay Connected